Website Security Audit: How to Protect Your Site From Security Breaches

The increasing number of cyber attacks makes a lot of website owners worry. Malware, DDoS, ransomware, and cross-site scripting are only a few examples of potential threats online.
These attacks usually target website vulnerabilities to steal sensitive information or jeopardize a website’s files and appearance. To mitigate the threat of cyber attacks, you need to perform website security audits as part of website maintenance and build an online security infrastructure.
This article will discuss how to perform website security audits and explain why they need to be performed regularly. We will also recommend seven great tools to scan your website and cover three excellent website audit services.
Download WordPress security checklist
What Is a Website Security Audit?
A website security audit is a process of examining your files, website core, plugins, and server to identify loopholes and potential vulnerabilities. Security audits include dynamic code analysis as well as penetration and configuration tests.
How to Perform a Website Security Audit: 7 Definitive Steps
Before performing a website security audit, it’s essential to identify the site elements that have to be examined. Here’s what you should add to your audit checklist:
- Website core files
- Extensions
- Software
- Themes
- Plugins
- Third-party components
- Server and site settings
- User settings and practices
- Plan and SSL renewals
- Website traffic
In this section, we’ll discuss the seven steps you should take to audit the security of these elements carefully.
1. Run a Security Scan
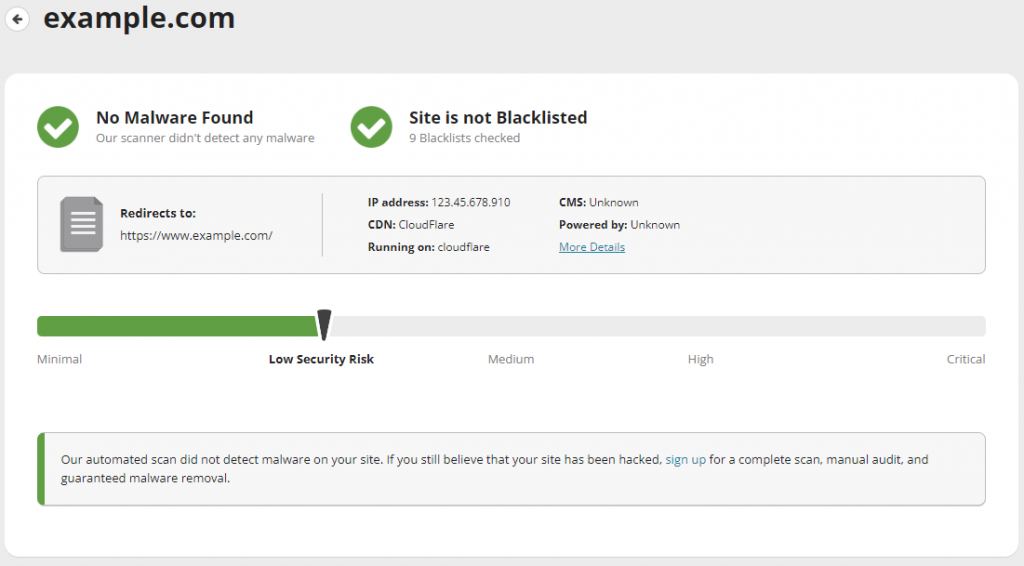
A security scan verifies whether a website is blacklisted and checks it for malware, errors, and outdated software. We recommend using Sucuri SiteCheck – just type in your domain name in the search bar and click Scan Website.
Sucuri will present a report and score the site, letting you know its security risk level. The tool also provides recommendations on what you should improve and identifies potential loopholes.
There are plenty of other tools to run a security scan of your website. Whichever you go for, it’ll lay the foundation for the rest of your site security audit.
2. Review Site Settings
The next element you should review is your site settings. If you use a content management system (CMS) such as WordPress, open your site’s dashboard. From there, verify the website’s configuration settings for potential vulnerabilities.
Here are some elements to keep an eye out and the steps WordPress users should take to improve their security:
- Comment settings. Moderate your comment section by filtering out spam comments. Using the Comments menu on the WordPress dashboard, you can mark comments as Spam or delete them entirely.
- Visible information. Hide the information related to the backend of your website. Hackers can use it to dig deeper into the site and find attack vectors for hacking. Only show the content that you intend for your users.
- Input validation. Implement validation for all sections of your site that accept user input. This means taking measures that prohibit the entry of certain characters. In addition, always use the latest version of WordPress, plugins, and themes.
3. Check User Accounts and Permissions
A web server will verify a user’s access privileges when they are trying to make changes to a website.
If you use WordPress, it is essential to organize user roles and permissions to manage the access to your website. Assign user roles and categorize their levels of permissions accordingly.
There are six roles available in WordPress – super admin, administrator, editor, author, contributor, and subscriber. Each has assigned permissions which include publishing, writing, managing, and configuration.
From the Users menu of the WordPress dashboard, check whether there are any unused or abandoned accounts. For your website security, delete them and ensure the rest of the accounts are protected with strong passwords.
4. Perform Regular Updates
Outdated components often contain vulnerabilities that might lead to a hacked website. It is important to regularly update your CMS, extensions, plugins, themes, and software.
Doing so will minimize the risk of cyber attacks, so make sure to dedicate some time to update important files whenever a new version of a website element or software is released.
5. Make Sure Your IP and Domain Are Secure
A domain or IP address may be blocklisted when it is directly involved in malicious activity, such as sending spam emails, distributing malware, and hosting phishing websites and botnets.
Some useful tools to check the reputation of a domain or IP address include Spamhaus and SpamCop. Both manage lists compiled by specialist research teams who have evaluated the listed internet resources.
If you find your domain or IP address on a blocklist, the next step is to request removal. However, if you use a shared server, then report the issue to your hosting provider. If the blocklisted IP address was issued by your internet service provider (ISP), contact the company instead.
We also recommend getting domain privacy protection if you haven’t got it. It will protect your WHOIS information from the public, preventing the possibility of malicious misuse.
6. Check for Any Plan or SSL Renewals
Be aware when certain services related to your website have to be renewed. Be sure to check the expiry date of your domain name, hosting plan, and SSL certificate so you can take action before your website becomes inaccessible or unsecure.
Depending on your registrar, a domain can be registered for up to 10 years. Meanwhile, any SSL issued after September 1st, 2020 is valid for up to 397 days (13 months) although the subscription period can be longer. Lastly, most hosting providers allow purchasing plans for as long as four years.

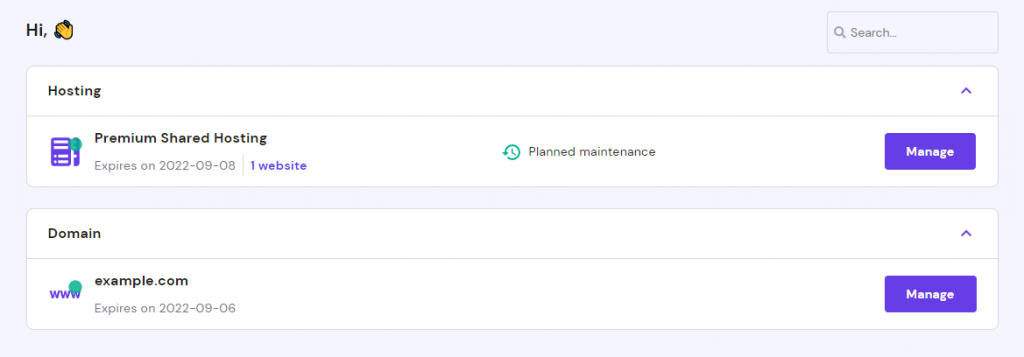
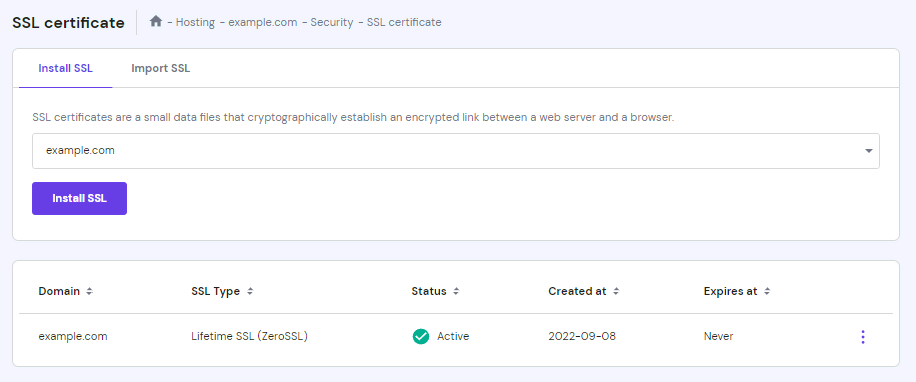
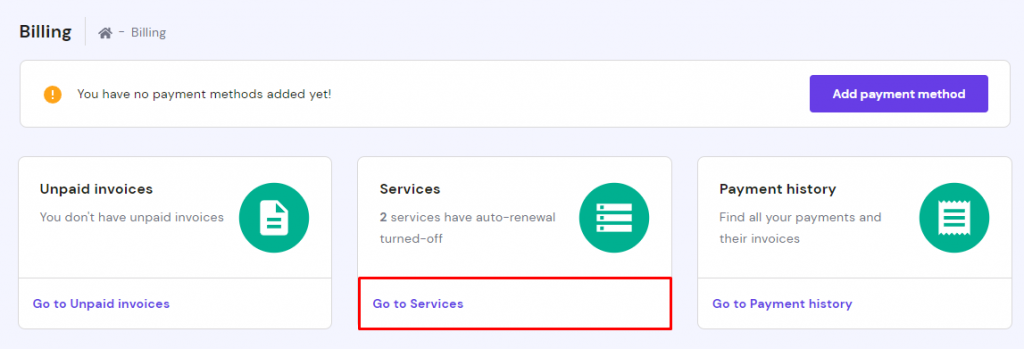
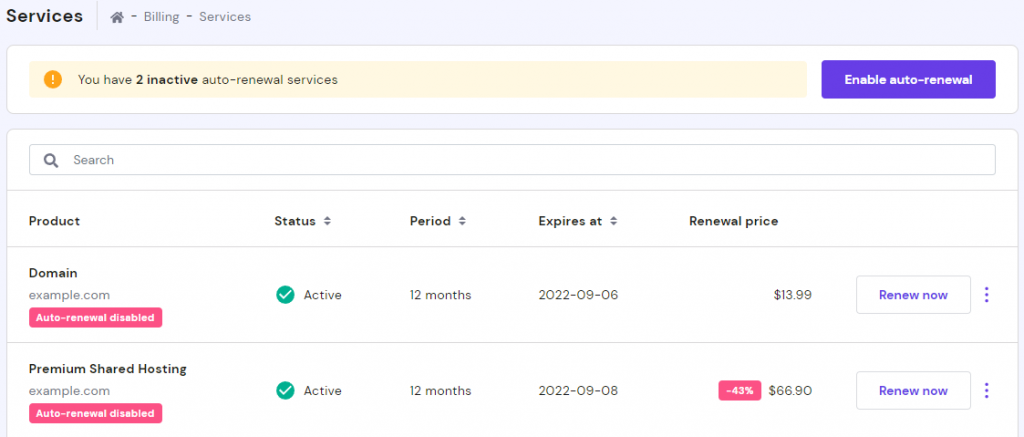
Here’s how to find out your domain, hosting plan, and SSL expiry dates and renew them on Hostinger:
- Access hPanel. The domain and hosting plan expiry dates will be visible under each service.
- To check when your SSL certificate expires, navigate to the SSL tab.
- To renew a service, switch to the Billing tab and select Go to Services.
- Choose a service and click Renew now.
- Choose a Billing period and select Choose payment method. Proceed with the payment on the new page.
- The system will generate a renewal invoice.
Alternatively, you can navigate to Billing –> Unpaid Invoices to see whether the system has already generated new invoices.
7. Assess Website Traffic
Website traffic is the amount of users visiting your website. It comes from three main sources:
- Direct source. Users type the URL in the browser.
- Referral source. Traffic that comes via links found on other websites, such as social media platforms.
- Organic source. Users who have used a search engine to find your website.
Some useful tools to check website traffic are Google Analytics, Ahrefs, and MonsterInsights.
Here are four tips to help you monitor your website traffic:
- Filter irrelevant traffic. Watch out for visitors who come from untrusted sites.
- Traffic location. If there’s a traffic spike in a certain location, either your content is truly popular in that area or computers there have been hijacked and are flooding your website with traffic it can’t handle.
- Big spikes. If your site experiences sudden increases in traffic and there’s no clear reason as to why, it might indicate botnet attacks.
- Huge drops. If your website’s traffic suddenly drops, test it and see if it’s running slowly. Another option is to check whether Google has flagged it as malicious. There’s a possibility that visitors can’t access it because they don’t see it listed in the search results anymore.
There are ways to prevent spikes of malicious traffic, such as using Cloudflare page rules. Once you’ve enabled it, Cloudflare will redirect or reject fake requests to keep your website online.
Suggested Reading
Top 7 Tools for Website Security Audit
There are many online tools – both free and premium – you can use to perform website security audits. In this section, we’ll cover the seven best online audit tools you should check out.
1. NordPass
Your website’s security can only be as strong as its password. NordPass is a tool that generates unique passwords and stores them in a personal vault which can be accessed on any device or browser. It offers three plans – Free, Premium, and Family.
The Free plan offers password manager service which will allow you to store any passwords inside the NordPass vault. The Premium and Family plans start from $2.49/month and $4.99/month, respectively, and include additional website security features such as protection from data leaks and password vulnerability identification.
2. Intruder
Intruder is an online vulnerability scanner that can examine websites and applications. It offers external and internal vulnerability scanners and continuous penetration testing. Intruder identifies issues in every security layer of a website and provides detailed security assessment reports that are ISO 27001 and SOC 2 compliant.
Unfortunately, Intruder doesn’t have a free version. Instead, there are three plans with different features available. Essential and Pro plans start from $101/month and $129/month for one website, respectively. The third plan, Vanguard, is priced upon request and includes support from a dedicated team of security professionals.
3. Observatory
Observatory is a free online website security audit tool from Mozilla. To use it, simply input your domain name in the search bar and press the Scan Me button. The tool will process the request and display the results in four tabs – HTTP Observatory, TLS Observatory, SSH Observatory, and Third-party Tests. Each one focuses on different aspects of website security and provides recommendations based on the evaluation.
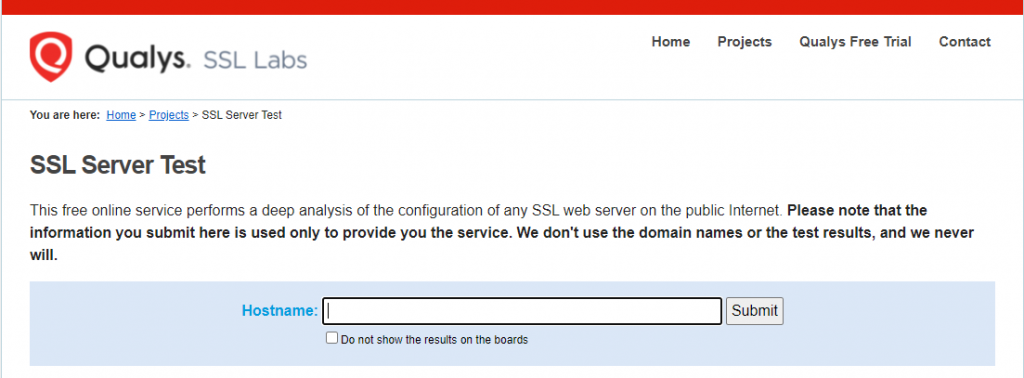
4. Qualys
SSL certificates are an important aspect of website security. Therefore, it is essential to check your SSL configuration especially after making any changes. Qualys’ SSL Server Test tool provides a deep analysis of a site’s SSL certificate and settings. Simply enter your domain name in the search bar and click Submit to start the scan.
Once finished, Qualys will display a summary of the SSL audit and score your website from A to D. The tool also features a ranking board that includes all recently scanned websites as well as the best and worst test scores. Consider ticking Do not show the results on the boards option if you don’t want your website to appear on it.
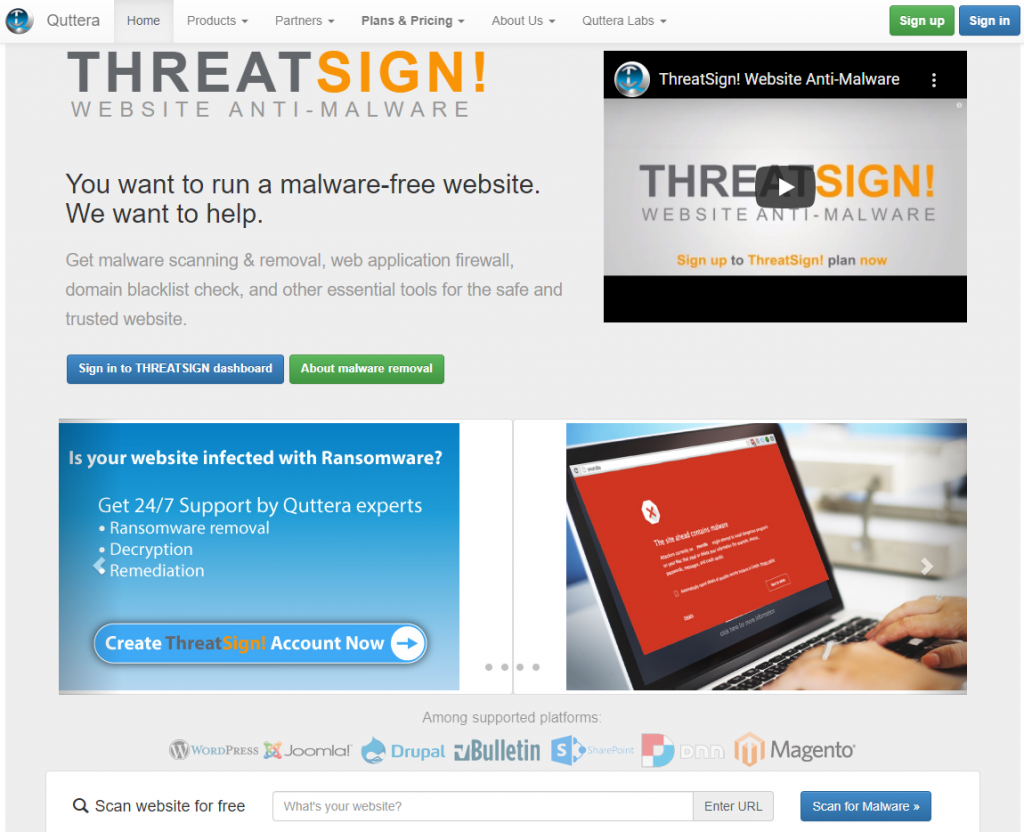
5. Quttera
Quttera is a tool that specializes in malware scans. You can scan your website for free by entering the domain name in the search bar and clicking Scan for Malware. Once finished, Quttera will let you know whether it detected any issues and provide an evaluation of the site, including its blocklist status and file analysis.
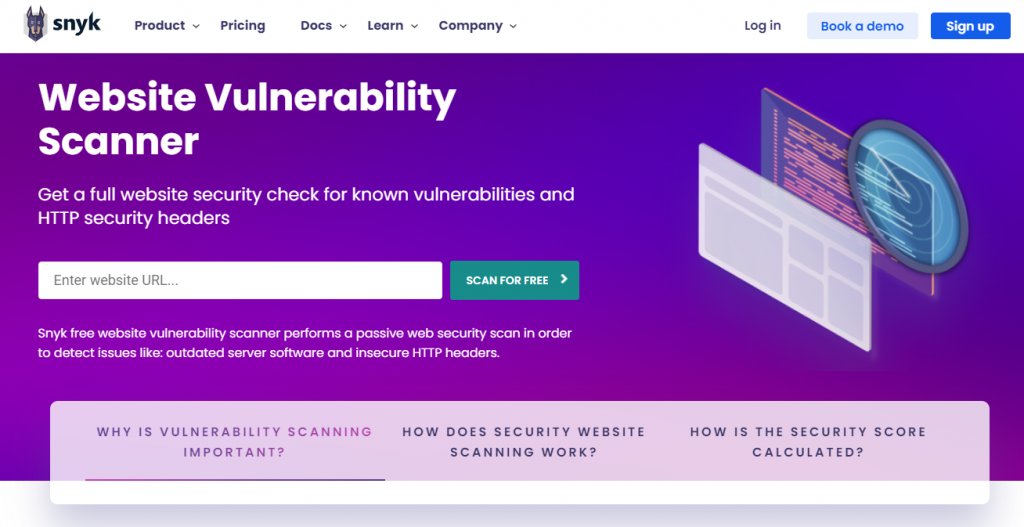
6. Snyk Website Scanner
Snyk features a website vulnerability scanner that will check your site for outdated server software and insecure HTTP headers. To use it, type your domain name in the search bar and click Scan for Free. Once the results are in, you will be able to check the score your site got along with detailed explanations.
A plus point for Snyk is that you can fix the issues as soon as the free audit ends using their tools. That said, the free version is quite limited. If you want a full scan with advanced solutions and tools, you’ll have to purchase a premium Snyk plan. It may not be the best option if you’re a solo webmaster – the Team, Business, and Enterprise plans are aimed at developer teams.
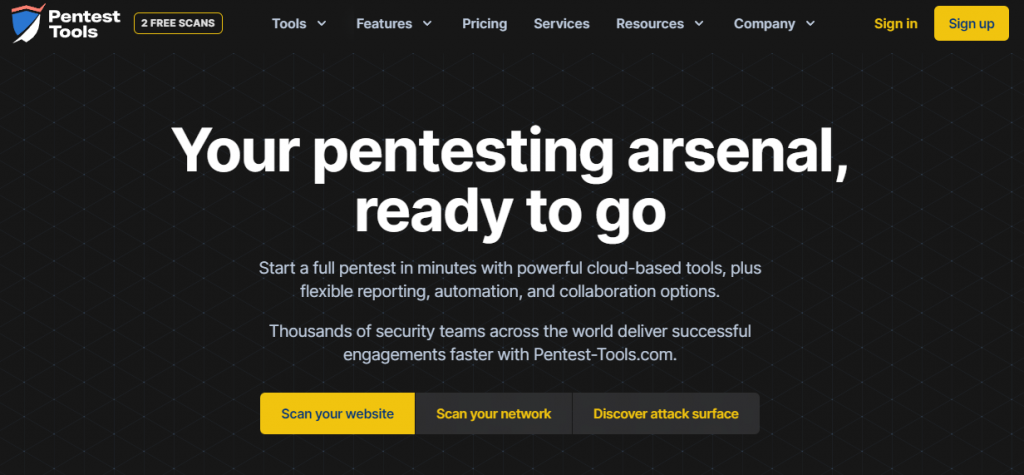
7. Pentest-Tools
Pentest-Tools features a scanner tool that assesses the security of various website elements. To use it, click Scan your website and choose Light scan. Finally, press Scan target. The results will be displayed in a downloadable report along with risk assessment information and important findings.
Unfortunately, the free version of Pentest-Tools has limited features and only allows one website scan per 24 hours. If you’re looking for an advanced tool with additional functionality, consider purchasing one of the premium plans which start at $93/month. There are four available – Basic, Advanced, Teams, and Enterprise.
Top 3 Services for Website Security Audit
There are many services available if you don’t want to perform website security audits manually. These will take care of the whole process, including detecting vulnerabilities, resolving the issues, and keeping the website secure.
In this section, we’ll discuss the three best website security audit services.
1. Burp Suite by PortSwigger
Burp Suite provides a web security audit toolkit, both manual and automated, depending on the plan you choose. It includes website vulnerability security audits, manual penetration testing, advanced/custom automated attacks, productivity tools, and extensions. Burp Suite comes in a form of Community, Professional, and Enterprise services.
The Community Edition is free and features a manual toolkit that you can download to your computer. The Professional plan starts at $399/user/year and offers both manual and semi-automated security testing tools. The Enterprise Edition starts at $6,995/year and includes additional automated tools and collaboration with the Burp Suite AppSec team.
2. Acunetix
Acunetix is an audit platform developed by Invicti Security that focuses on web application security testing. It’s trusted by more than 2,300 companies worldwide, such as American Express and AVG.
Acunetix offers advanced features such as scheduled vulnerability assessment, Interactive Application Security Testing (IAST), and Continuous Integration and Delivery (CI/CD). In order to obtain a quote, you will need to fill out a form on the website – the Acunetix sales team will follow up with their suggestions and prices.
3. Security Brigade
Security Brigade provides a wide array of services including manual and automated security audits, in-depth vulnerability reports, and web and mobile application testing. It counts well-known brands like Domino’s, Sephora, and Cisco among its customers.
Security Brigade will personalize the website security checklist based on the scope of your work and business objectives. To purchase the service, you’ll need to fill out a contact form and the Security Brigade team will follow up with a proposal and price. If you’re not certain, a free demo of each of their services is available.
Suggested Reading
If you’re a WordPress user, check out the best WordPress security plugins
Why Do You Need to Do Website Security Audit
Websites with weak security infrastructures are prone to cyber attacks. If your website gets hacked, your data – including sensitive customer information – is at risk of being stolen. This can have severe financial consequences and result in lost reputation and trust.
To prevent this, perform regular website security audits so you know which elements of your site need work.
Here’s a list of common types of cyber attacks:
- Malware. Malware or malicious software is a program or code that damages the infected computer, network, or server. There are many types of malware, including ransomware, trojans, viruses, bots, and spyware.
- Ransomware. Ransomware is malware that demands payment from users trying to access their system. Paying does not guarantee that access will be restored.
- DoS and DDoS attacks. Such cyber attacks aim to overload a network or server by sending multiple fake requests. DoS attacks usually come from one system while DDoS are initiated by multiple threat actors.
- Cross-Site scripting (XSS). Cross-Site scripting occurs when a third party inserts malicious code into a website. When the infected script runs, hackers may try to steal sensitive information or damage the site.
- SQL injection. This happens when a hacker injects a malicious SQL statement into an application’s queries that connect to the database, enabling hackers to access, modify or delete the system data.
If your website retains personally identifiable information (PII) from your visitors, you have to perform regular website security audits as part of security requirements. There are laws that regulate the retention and distribution of private information.
Here’s a list of data privacy regulations you may need to adhere to depending on your location:
- General Data Protection Regulation (GDPR). The GDPR is a set of rules on protection of private information for people in the European Union.
- Payment Card Industry Data Security Standard (PCI DSS). PCI DSS is a set of information security standards for the safety of cardholder data worldwide.
- California Consumer Privacy Act (CCPA). CCPA is a California state law that regulates privacy rights and consumer protection.
- The Sarbanes-Oxley Act (SOX). SOX is a United States law that regulates financial record keeping to increase the accuracy of fiscal reporting and to protect investors from fraud.
Pro Tip
In your security audit, don’t forget the website security software integrated with your hosting service. These tools play a crucial role in safeguarding your site from various threats. Ensure that your security setup, whether it’s part of your hosting package or an additional service, is robust and tailored to your website’s specific security requirements.
Conclusion
A number of webmasters focus on making their websites as interesting as possible, while others optimize them for maximum performance, but fail to notice security loopholes and vulnerabilities. Not equipping a site with sufficient security measures is a bad idea as it may be prone to cyber attacks. Therefore, perform regular web security audits to protect your website and manage its vulnerabilities.
We have discussed the seven steps to perform a security audit. That includes regular security scans and software updates, site settings reviews, and making sure your subscriptions are renewed.
If you need help, there are plenty of online tools you can use to detect security vulnerabilities. We’ve discussed the seven best tools for web security audits you should check out, including NordPass, Intruder, Observatory, and Qualys. Make sure to consider your needs and budget before choosing one.
Alternatively, you can purchase a subscription to a web security audit service that will take care of everything for you. We recommend checking out Burp Suite by PortSwigger, Acunetix, and Security Brigade.
Make sure to opt for secure hosting plan to protect your site. Hostinger, for instance, provides anti-malware software such as Monarx in their plans.

We hope this article has helped you understand website security audits and how to do them. If you have any questions or suggestions, please leave them in the comment section below.